Mobile devices continue to be the target of attack at increasing rates. There is a relatively simple explanation for this – in a typical organization today, 60% of the endpoints containing or accessing enterprise data are mobile; the majority of which do not have any mobile threat defense.
Mobile devices contain or have access to the same information as traditional endpoints. While billions of dollars have been spent protecting and securing traditional endpoints, very little has been invested to protect mobile device endpoints.
These were the key findings according to Positive Technologies’ yearly report, Vulnerabilities and Threats in Mobile Applications 2019:
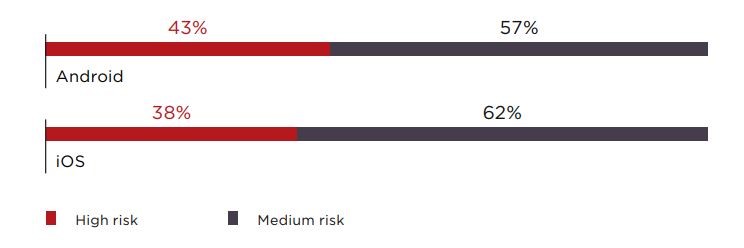
Fig. Positive Technologies’ Mobile App Vulnerabilities and Threats 2019 Report
- Insecure data storage is the most common issue, found in 76% of mobile applications.
- Hackers seldom need physical access to steal data: 89% of vulnerabilities can be exploited using malware.
- Most cases are caused by weaknesses in security mechanisms (74% and 57% for iOS and Android apps, respectively, and 42% for server-side components).
The Solution
A revolutionary Mobile Threat Defense engine that uses machine-learning to detect device, network, phishing and application mobile attacks on-device and in real time. The engine was specifically developed for mobile, not ported from traditional endpoint security, to guard against the unique threats targeting iOS and Android devices.
How it works
By analyzing slight deviations to the mobile device’s OS statistics, memory, CPU and other system parameters, the solution can accurately identify not only the specific type of malicious attack, but also provide forensics associated with the who, what, where, when and how of an attack occurrence
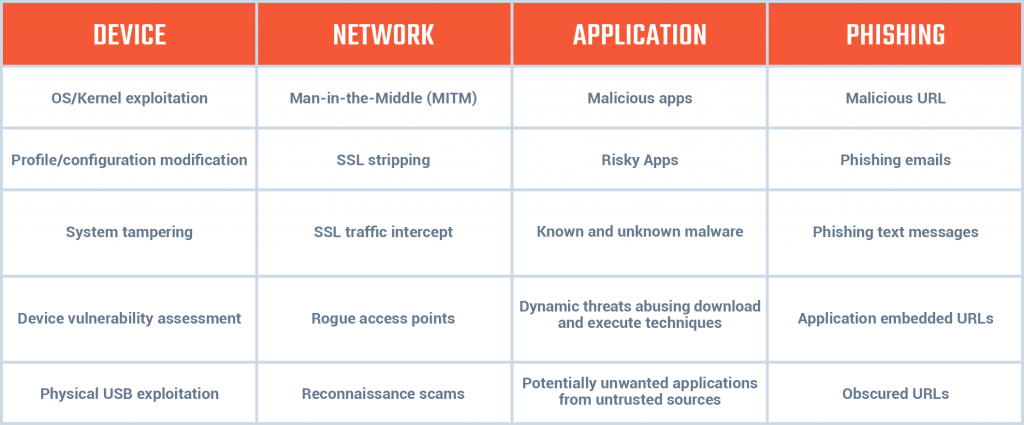
Fig. Types of Mobile Threats
Stop Zero-Day Threats without Signatures or Lookups
The entire mobile device is monitored for malicious behaviour regardless of the attack entry point. The device-wide resident approach does not rely on external IDs or malware signatures, and does much more than app scanning.
Read More: Zimperium’s Mobile Application Suite (MAPS)