Protecting email data from unauthorized access is key part of every organization’s zero trust strategy especially when email remains the most pervasive form of corporate communication. It’s also the #1 source of data leaks. Seamless email encryption is the answer.
The move to the cloud, heightened requirements to share business information, and an increasingly complicated regulatory environment have permanently increased the stakes for email protection. Perimeter-based approaches continue to leave enterprises vulnerable, causing security teams using best practices to prioritize data-centric, end-to-end protection
However, securing email does have its challenges. The user experience has been greatly fraught by clunky software where users need to follow a complicated process before an email can be secured. To work around this, organizations have turned to a cloud service provider to manage emails and host sensitive files centrally where the attachments are shared via a link. Now, this presents another problem where confidential information in the cloud (instead of in your own premise) is at the mercy of cloud service provider.
5 Must-Have Features for Modern Email Encryption
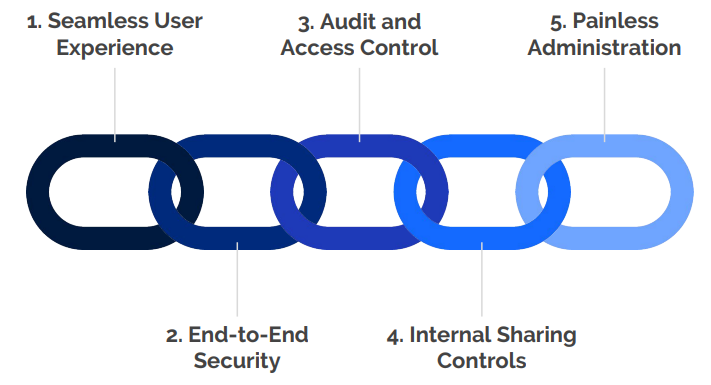
To meet today’s information sharing requirements, organizations must adopt email protections that shield critical business data and provide flexible controls, while supporting extremely usable workflows for end users and administrators. User experience, security, audit and access control, internal sharing controls, and administration are all must-have features of a secure email encryption solution that meets modern enterprise requirements.





